Optionsbleed and some fun with editors and HTTP leaks.
Hanno Böck
https://hboeck.de/
Twitter: @hanno
HTTP
HTTP uses "methods", a normal HTTP request is a GET, a form submission is usually a POST.OPTIONS
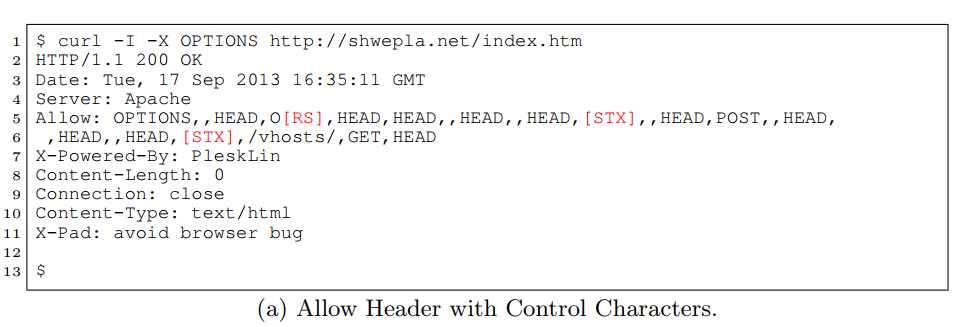
Shows you which HTTP methods a server supportsAllow: ,GET,,,POST,OPTIONS,HEAD,, Allow: POST,OPTIONS,,HEAD,:09:44 GMT Allow: GET,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,, HEAD,,HEAD,,HEAD,,HEAD,POST,,HEAD,, HEAD,!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd" Allow: GET,HEAD,OPTIONS,=write HTTP/1.0,HEAD,,HEAD,POST,,HEAD,TRACE
 Support for Various HTTP Methods on the Web, Arxiv, 2014-05-08
Support for Various HTTP Methods on the Web, Arxiv, 2014-05-08
Optionsbleed was already discovered in 2014, but nobody noticed it's a security problem.
One month after Heartbleed!

Editors and Web leaks
Backup files
config.php~
VIM
.config.php.swp
JOE
DEADJOE
Nano
config.php.save
EMACS
#config.php#
HTTP does not support files with # in them.
Thanks for listening!
https://hboeck.de/Twitter: @hanno