Attacking with HTTP requests
Finding stuff on web servers
Hanno Böck
https://hboeck.de/
Twitter: @hanno

GIT
https://example.com/.git/config
https://github.com/internetwache/GitTools

Golem, 2017-05-17
VIM
vim wp-config.php creates a temporary file .wp-config.php.swp
https://example.com/.wp-config.php.swp
https://example.com/wp-config.php~
Database dumps
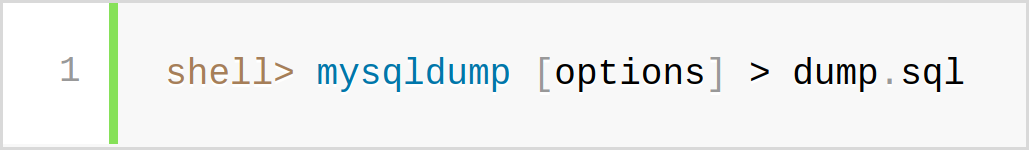 MySQL documentation - mysqldump
MySQL documentation - mysqldump
https://example.com/dump.sql
Database with 600,000 addresses from Australian online pharmacy.
Zeit Online, 2017-07-05
Private Keys
https://example.com/example.com.key
Let's talk about cryptography (don't be scared)
Keys are just large numbers
Public and Private Keys (RSA)
- Public key: N, e
- Private key: N, e, d, p, q, dP, dQ, qinv
RSA private key: the same N and e and some more numbers.
Good idea?

Hanno's blog, 2017-07-20
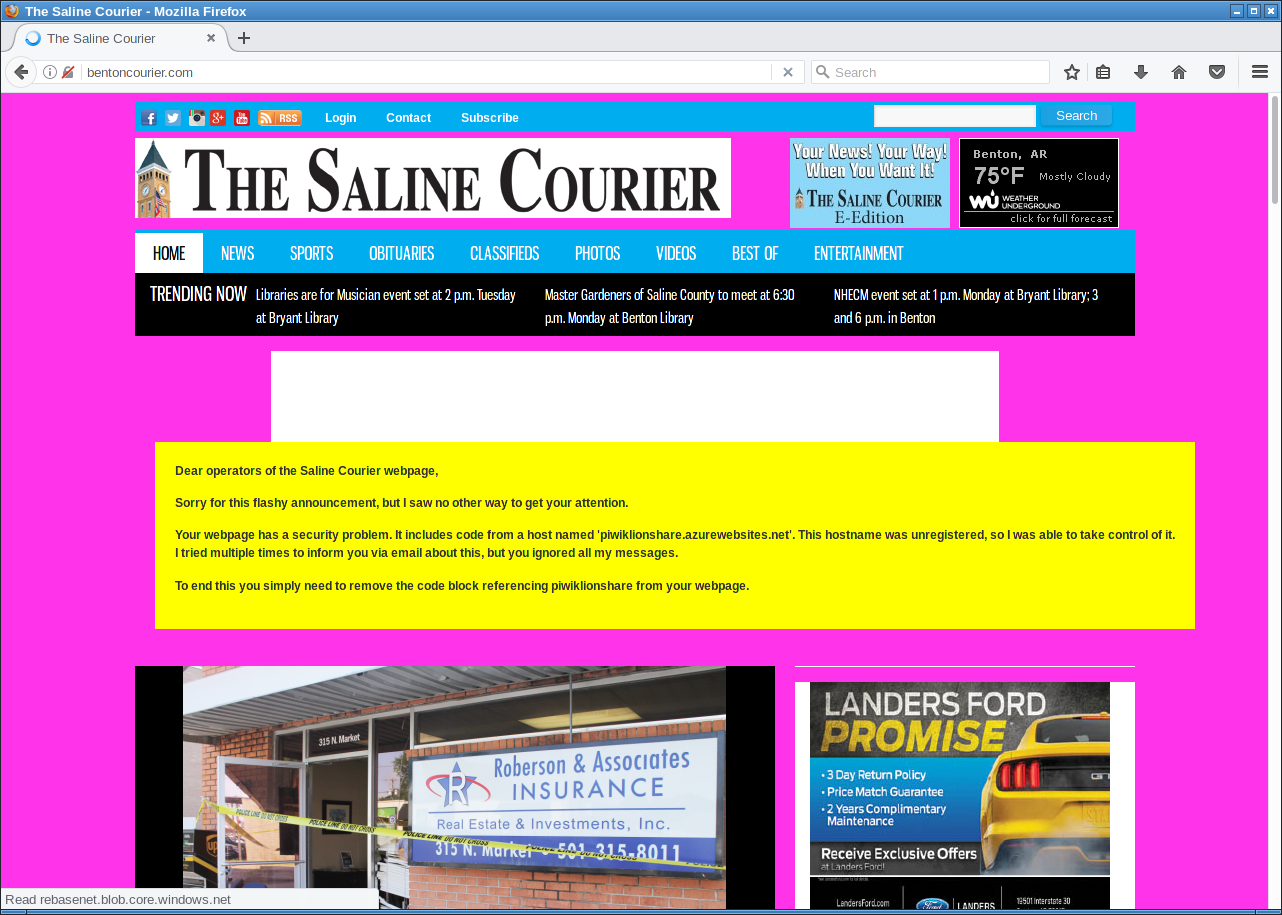
Abandoned Domain takeover
<script type="text/javascript" src="https://example.org/fancy.js"></script>
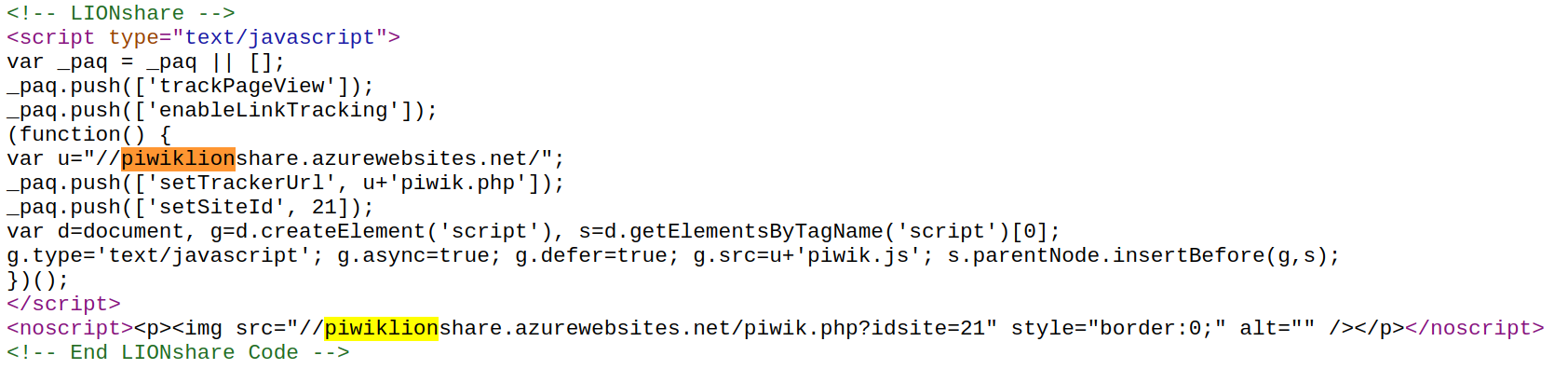
Most removed code after contacting them.
HTTP
HTTP uses "methods", a normal HTTP request is a GET, a form submission is usually a POST.OPTIONS
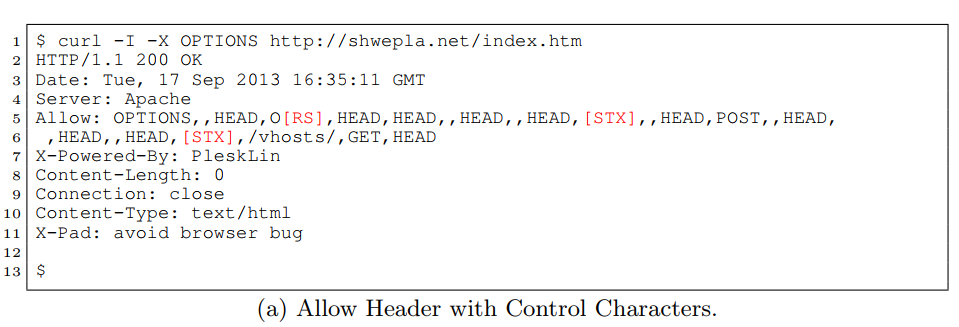
Shows you which HTTP methods a server supportsAllow: ,GET,,,POST,OPTIONS,HEAD,, Allow: POST,OPTIONS,,HEAD,:09:44 GMT Allow: GET,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,, HEAD,,HEAD,,HEAD,,HEAD,POST,,HEAD,, HEAD,!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd" Allow: GET,HEAD,OPTIONS,=write HTTP/1.0,HEAD,,HEAD,POST,,HEAD,TRACE
 Support for Various HTTP Methods on the Web, Arxiv, 2014-05-08
Support for Various HTTP Methods on the Web, Arxiv, 2014-05-08
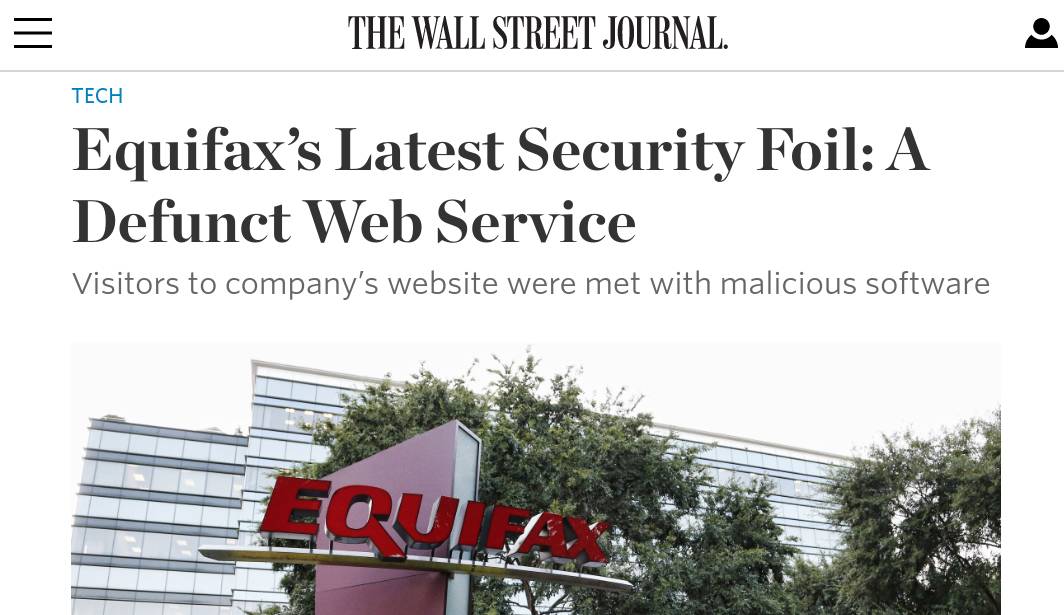
Optionsbleed was already discovered in 2014, but nobody noticed it's a security problem.
One month after Heartbleed!

Summary
- Don't put secret stuff on web servers
- Sometimes simple attacks are the best
- Have more ideas? Talk to me!
- I'm gonna release a tool to scan for all these issues soon.
Thanks for listening!
https://hboeck.de/Twitter: @hanno